Allow Remote Debugging of Docker Containers
When remotely debugging linux docker containers, the account that your remote debugging session uses to SSH into the Linux host must have RW access to the docker.sock process.
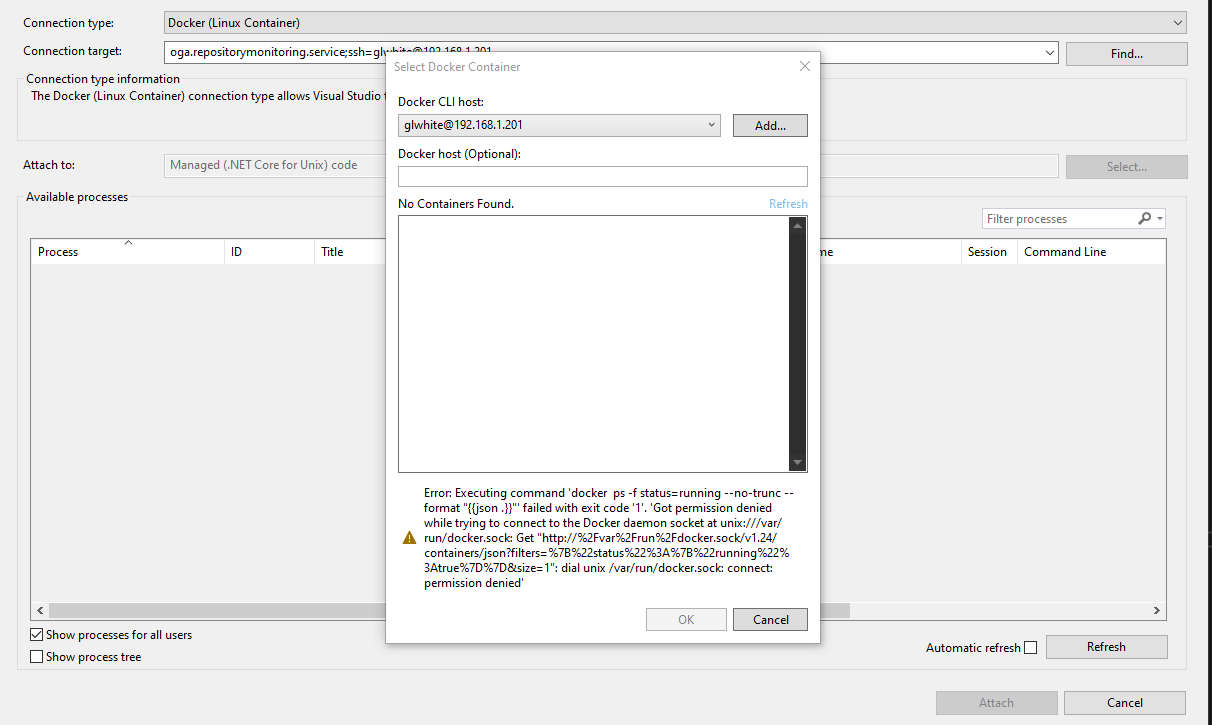
If the permission is not granted, you may see an error like this:
The above error means that (barring an SSH connection problem) the user account cannot communicate with the docker socket.
Granting permission to the remote debugger user can be done with either of the below ways:
Adding to the Docker Group
You can add the user to the docker permission group:
sudo usermod -aG docker $USERNOTE: The above assumes that docker.sock allows RW permissions to the docker docker group.
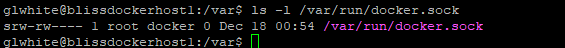
You can check this by listing the directory entry of docker.sock:
The above shows that members of the 'docker' group have RW access to docker.sock.
So, adding your SSH user to that group, allows access.
Open Permissions for docker.sock
This method creates a security vulnerability that may give anyone on the system, access to docker resources or allow commands.
If adding your SSH user to the docker group fixes the problem, stop here.
Use this method if changing the group access does not work, and you can mitigate the security hole of opening permissions to other users on the host.
The legacy method would be to open filesystem permissions on the docker.sock file like this:
sudo chmod 666 /var/run/docker.sockOr, by changing permission on the symbolic link in /run, if your distro maps /var/run to /run with a symbolic link of the entire folder:
sudo chmod 1666666 /run/docker.sock